If check_policy is on,
- check_expiration is also on, unless set to off explicitly
- Password history is initialized with the value of current password hash
- check_expiration is set to off
- Password history is cleared
- Value of lock_out time is reset
If check_policy is on,
What can the roles do
Principals are entities that can request resources. Principal can either be an individual or a collection. A Windows Login is an example of an indivisible principal, and a Windows Group is an example of a principal that is a collection.
sys.database_principals gives a list of all the principals
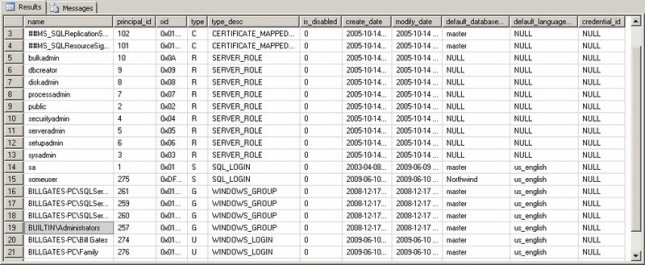
Windows-level principals
SQL Server-level principal
Database-level principals
Tail Log backups will backup those transactions in the log file which have not yet been backed up since the last backup.
In case of a disaster of a database, and a point in time recovery is needed, a tail log backup must be taken first. If you begin to restore the database first, the opportunity to restore thail log of the backup is forever lost.
Not all restore scenarios require a tail-log backup. You do not have to have a tail-log backup if the recovery point is contained in an earlier log backup, or if you are moving or replacing (overwriting) the database and do not need to restore it to a point of time after the most recent backup.
Source: http://msdn.microsoft.com/en-us/library/ms179314.aspx
This is a table in the msdb database. It contains a single row for each backup set. A backup set contains the backup from a single, successful backup operation. You can get information regarding the size of a backup vs the compressed backup size.
SQL Server only backs up the data pages in the database that have been used currently. So a full backup is generally smaller than the database size
You can use sp_spaceused to estimate the full backup size by subtracting the unallocated space from database_size
Source: Pro SQL Server 2008 Administration by Ken Simmons and Sylvester Carstarphen
Source:
BOL http://msdn.microsoft.com/en-us/library/ms175477.aspx
MCTS 2008 – Training Kit – Mike Hotek
Uses: